There’s a lot you can do to browse the web anonymously and avoid being tracked by every website you visit. But no matter what you may have set, the browser can easily become be a leaky faucet when it comes to identifying personal details that could then be exploited by attackers for financial gain. Here’s how your browser might be compromising your privacy and what you can do about it.
1. Minimize the use of browser extensions
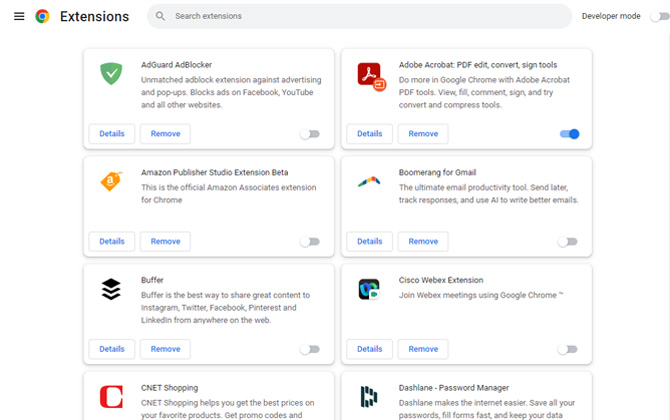
The web is rife with downloadable software designed to give your browser additional powers. These include extensions that show you whether reviews are fake, correct your grammar and much more. Unfortunately, these extensions can be riddled with vulnerabilities that hackers may exploit for a land grab at your personal info. And when developers fail to update their extensions, people who use them can become targets.
Head into your browser settings to see what extensions you have downloaded and disable those you infrequently or never use.
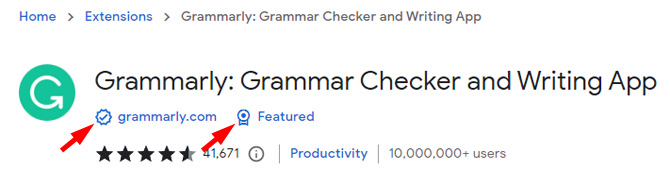
There are good extensions that enhance your online experience. To make those extensions easy to find, in April, Google started placing badges on extension listings in the Chrome store to indicate the extension is from a trusted publisher. The checkmark badge next to the name of the developer indicates that the developer is an Established Publisher with a good record and has had no history of violations. The Featured badge means that the extension follows Google's technical best practices for the user experience and design.
What to do
2. Dodge browser fingerprinting
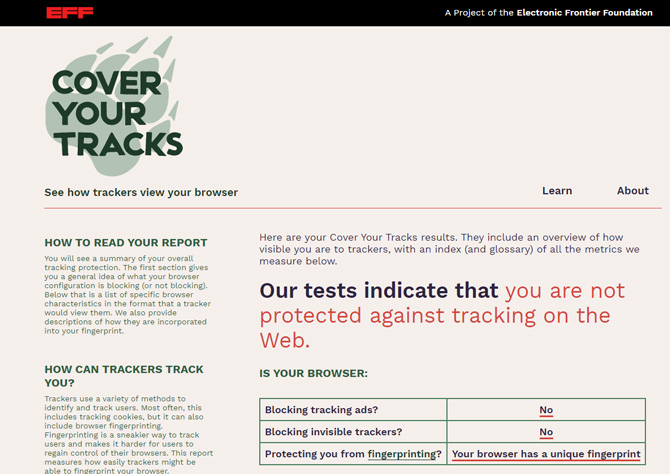
Websites often query your browser for data such as location, hardware, screen size, installed fonts and browser version, so they’re able to load the web pages correctly. However, this list combines to make a “fingerprint” that’s overwhelmingly unique to your browser, making it highly trackable even if you’ve disabled trackers.
See how unique your browser is at Cover Your Tracks, a browser tester set up by the Electronic Frontier Foundation. The site will tell you how unique your fingerprint is and whether your browser is blocking ads and invisible trackers.
What to do
There’s not a lot you can do about browser fingerprinting. In theory, protection from fingerprinting involves a device with the same settings and programs as the most other people. For example, an iPhone would offer better protection than an Android because it has less ability to be customized and made unique; a Chrome user would be less unique than, say, a Linux user.
Chrome, Edge, and Firefox users could try extensions that randomize what data is reported by the browser, because presenting a different fingerprint every time makes tracking impossible. Chameleon (Firefox) and Random User Agent (Chrome and Edge) have decent reviews at their respective app stores.
3. Prevent phishing attacks on browser autofill
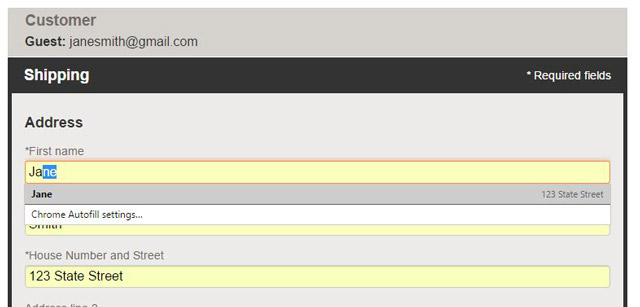
Your browser’s autofill function exists to make it easier and faster to fill in forms that ask for the same tedious information – your name, address, and date of birth. The convenience of saving such information often outweighs any concerns you may have over the security chops of a browser.
However, in the past, browsers have been tricked into revealing saved personal information without the user realizing it. This phishing attack would occur via hidden text boxes coded into a malicious site, alongside a couple of visible requests for innocuous information like your name and email address – say, a pretense at getting a discount offer. When you type in the info, the autofill feature ends up adding other information saved to the browser autofill, which could include enough details to enable credit card fraud.
What to do
Avoid typing in any personal information on websites you’re not sure about. Delete credit card information from your browser, or turn off the autofill feature entirely. Here’s how.
Chrome: Settings > Autofill > Payment methods to remove credit card information and Settings > Addresses and more to remove your address.
Edge: Settings > Profiles > Personal info to remove your address and other information you have stored for autofill.
Safari: Preferences > AutoFill. Manage what information is autofilled and delete or edit what’s saved.
Firefox: Settings > Privacy & Security > Forms and Autofill. Click in the box to remove the check mark for information you don't want autofilled.
4. Avoid sites that don’t use the HTTPS protocol
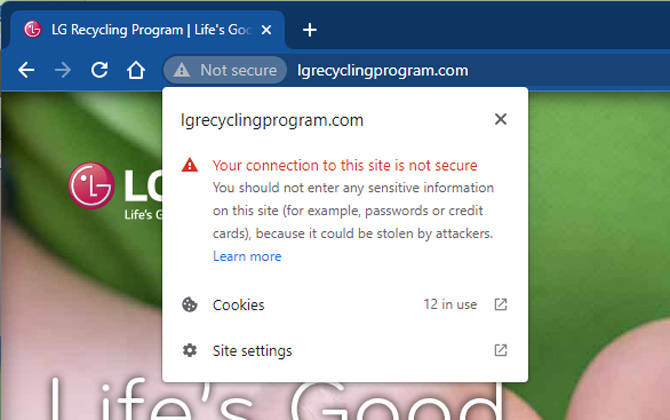
Heading to a website that doesn’t have the “https” prefix means anything you do there is unencrypted. This includes what you click as well as what you type – it’s all visible to any eavesdropper. While that shouldn't be a concern for public content sites where you are simply reading information, it should be a big concern on any site where you are entering personal information such as login credentials, social security numbers, or any other information you would not want snoopers to see.
Some websites may include the https prefix on their home page, then default to the unencrypted “http” on other pages. Things get especially dicey when you’re at a site where you need to log in with a password or input payment details.
Chrome, Edge, Safari and Firefox all flag sites as Secure with a padlock if they are fully encrypted or Not Secure (or a padlock with a red line through it) if they’re unencrypted. The alert appears on the left of the URL box.
What to do
Check for the padlock before entering any log-in or payment information.
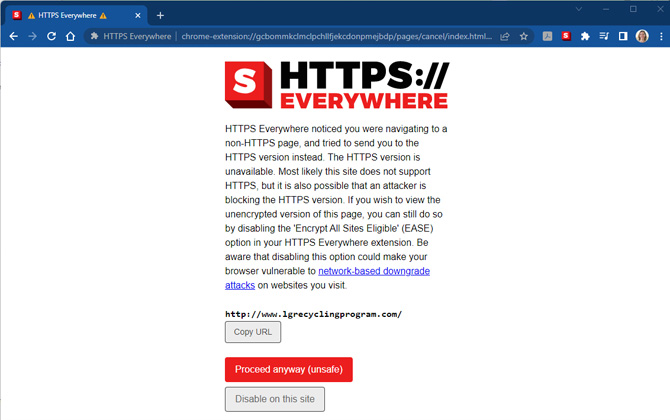
Download the HTTPS Everywhere extension for Firefox, Chrome, and Edge which automatically encrypts your browser’s communications with major websites if it finds faulty HTTPS links. Note that the extension can't force all connections to be https.
Updated on 7/1/2022
[Image credit: Screenshots via Techlicious, desktop computer via Smartmockups]
Natasha Stokes has been a technology writer for more than 10 years covering consumer tech issues, digital privacy and cybersecurity. As the features editor at TOP10VPN, she covered online censorship and surveillance that impact the lives of people around the world. Her work has also appeared on NBC News, BBC Worldwide, CNN, Time and Travel+Leisure.

















From T on July 07, 2019 :: 3:40 pm
Thanks for the article. Also there’s a lot more information that could be used for fingerprinting other than what Panopticlick shows, like on Device Info https://www.deviceinfo.me for proof of concept.
Reply