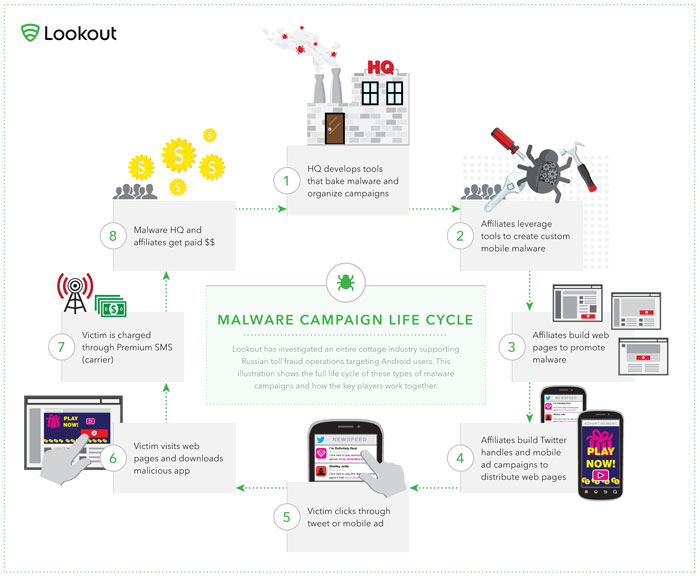
Security company Lookout announced they have uncovered a massive Android SMS fraud network accounting for 60% of the Russian malware they have observed in the wild. The investigation, dubbed "Dragon Lady", found 10 malware “Headquarter” organizations that operate as sophisticated affiliate networks for manufacturing, distributing and marketing premium SMS malware.
According to Lookout, there are thousands of individual distributors and potentially tens of thousands of affiliate websites promoting the malware. And marketers associated with the network can earn as much as $12,000 a month from these scams—quite a sum in Russia, where the average monthly salary is around $800. The affiliate networks even have gamification features, with leaderboards and badges for those bringing in the most money, and their own newsletter and blogs.

To pull in victims, the main channel is Twitter where they promote links to popular applications such as Skype or to free porn, videos, pictures and MP3s. Lookout identified more than 50,000 unique Twitter handles involved in the malware scams.
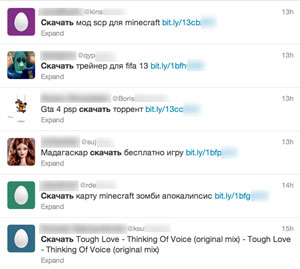
Fortunately, for those of us in the US, this specific threat is purely a Russian and Eastern European problem. The landing pages used by the malware affiliates are built to filter out any visitors from outside their targeted countries. And the SMS toll codes only work with Russian carriers.
But the lessons for smartphone users are the same no matter where you live. Most importantly, only download apps from places you know and trust (e.g., the Apple iTunes, Google Play or the Amazon App Store). If something appears too good to be true—get Netflix without monthly fees!—it probably is. And while anti-malware apps showed mixed results in our recent spyware test, using one of the better ones (go for one of the free versions that performed well in our test) is a wise safety measure.