Recently, Techlicious received a handful of posts in our comment section claiming that one of our images is violating copyright. We take copyright very seriously, so these posts immediately got my attention. But what I discovered could have actually been much worse – there was no copyright issue, it was all a ruse to trick us into installing a ransomware trojan that could have significantly disrupted our business.
Fortunately, I'm very familiar with how to recognize malware and scams, in general. But it would be easy for someone who isn't technically sophisticated to be fooled by these hackers and put their company's systems at risk.
Here are a couple of examples of the posts we received in the Techlicious comments [with Google Site URL removed]:
Hi!
My name is Jessica.
Your website or a website that your company hosts is infringing on a copyright-protected images owned by myself.
Check out this document with the links to my images you used at www.techlicious.com and my earlier publications to get the evidence of my copyrights.
Download it now and check this out for yourself:
https://sites.google.com/view/[redacted]
I believe you have willfully infringed my rights under 17 U.S.C. Section 101 et seq. and could be liable for statutory damages as high as $150,000 as set forth in Section 504(c)(2) of the Digital Millennium Copyright Act (”DMCA”) therein.
This letter is official notification. I seek the removal of the infringing material referenced above. Please take note as a service provider, the Digital Millennium Copyright Act requires you, to remove or disable access to the infringing materials upon receipt of this notice. If you do not cease the use of the aforementioned copyrighted material a lawsuit will be commenced against you.
I have a good faith belief that use of the copyrighted materials described above as allegedly infringing is not authorized by the copyright owner, its agent, or the law.
I swear, under penalty of perjury, that the information in the notification is accurate and that I am the copyright owner or am authorized to act on behalf of the owner of an exclusive right that is allegedly infringed.
Best regards,
Jessica Martin
and
Hi there!
This is Melangelle and I am a qualified photographer and illustrator.
I was baffled, to put it nicely, when I came across my images at your website. If you use a copyrighted image without an owner's permission, you must know that you could be sued by the owner.
It's not legal to use stolen images and it's so mean!
Check out this document with the links to my images you used at www.techlicious.com and my earlier publications to obtain the evidence of my legal copyrights.
Download it right now and check this out for yourself:
https://sites.google.com/view/[redacted]
If you don't delete the images mentioned in the file above during the next several days, I'll file a to your hosting provider letting them know that my copyrights have been severely infringed and I am trying to protect my intellectual property.
And if it doesn't help, trust me I am going to take it to court! And I won't give you a prior notice again.
On first blush, that sounds pretty scary and is likely to get many site owners to click on the link to learn more about the details of the accusation. When you do, you will be served a webpage with a link to file with your "copyright infringement evidence."
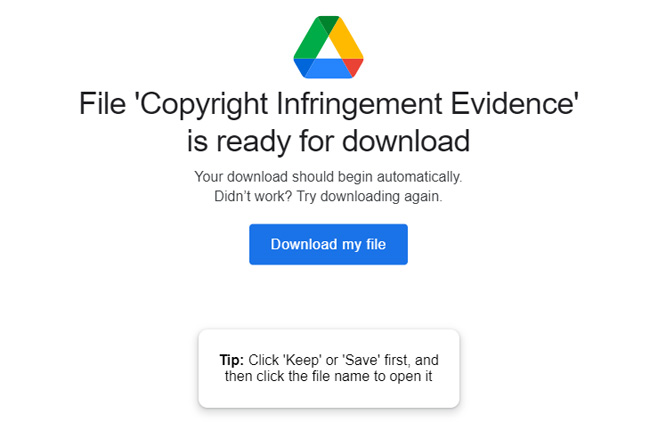
In the version of the scam we received, the download is a .zip file containing a javascript (.js) file called "Copyright Infringement Evidence.js". I ran the file through Virus Total and it came back as a backdoor trojan – identified as js.Trojan.Cryxos.5779 and JS/Kryptik.BXN – that can be used to install ransomware and other malicious programs. Only 8 of the 61 malware scanning engines in Virus Total picked this up (BitDefender, Emsisoft, eScan, ESET-NOD32, FireEye, GData, MAX, NANO-Antivirus), meaning it currently has a high chance of slipping through most antimalware protection.
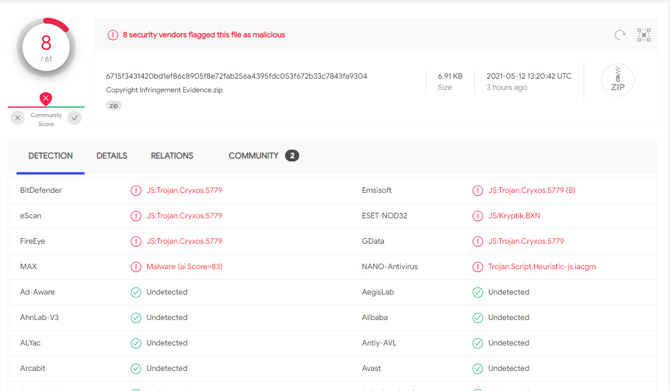
[EDITOR'S NOTE 8/12/2021: recent versions of this attack sent in by users are even more effective at evading antimalware protection. One sample was only picked up by a single vendor, NANO-Antivirus, a Russian-based antimalware organization, as Trojan.Script.Heuristic-js.iacgm. See: https://www.virustotal.com/gui/file/f2eeebca7c5d232cb4dce3698339a587ae6dc7cc98906d86573fe09a196ed95e/detection]
While this ransomware attack was directed against Techlicious through site comments, I can easily see the same attack method being attempted through email [EDITOR'S NOTE 5/13/21: readers are reporting in the comments below that the hackers are submitting these attacks through site Contact Us forms, as well.]. So it's an important reminder to be especially cautious when downloading any files from unknown third-parties or sites, and never try to open any file with an extension of .js or .exe unless you know exactly what it is and where it came from. To learn more, read our 5 tips to protect yourself against ransomware. You can also report the malware page to Google's malware reporting tool.
If you've received a similar message (on your site or via email), please post in the comments below [with the malware URL and any contact information redacted] so others will find it when doing a Google search and avoid the risk of having their systems compromised.
[Updated 5/25/2021 with information on Google malware reporting]
[Image credit: Smartphone on keyboard via BigStock Photo, screenshots via Techlicious]
Josh Kirschner is the co-founder of Techlicious and has been covering consumer tech for more than a decade. Before founding Techlicious, he was the Chief Marketing Officer for Inform Technologies, a start-up provider of semantic technology to media companies. Prior to Inform, Josh was a SVP and Managing Director in the financial services industry. Josh started his first company while still in college, a consumer electronics retailer focused on students.
















From Simon on June 10, 2021 :: 8:48 am
I’ve had a fair few on our website now - almost daily.
Reply